What Tech YouTubers Get Wrong About Audience Targeting

Building a successful tech YouTube channel involves more than just posting high-quality videos. Many creators focus heavily on content creation while overlooking one of the most critical aspects of growth: accurately targeting the audience. Misunderstanding who your viewers are can lead to wasted effort, low engagement, and slow growth. Some beginners turn to shortcuts for visibility, and while using services from the best site to buy YouTube subscribers may provide early momentum, long-term success depends on understanding the right audience. By identifying common targeting mistakes, tech creators can reach viewers who genuinely value their content, increase watch time, and establish a loyal community for sustainable channel growth.
Focusing on Too Broad an Audience
A frequent mistake is trying to appeal to everyone. Tech is a wide field, and attempting to cover all sub-niches dilutes your channel’s identity. New creators often produce content spanning smartphones, laptops, software, and gaming without defining who benefits most from their videos. This scattergun approach can confuse viewers and hinder algorithmic recommendations. Successful tech YouTubers identify a clear sub-niche and create content that resonates specifically with that audience, which improves engagement and retention rates. Defining an audience’s interests, age, and experience level ensures content reaches viewers who are most likely to subscribe and interact.
Ignoring Audience Analytics
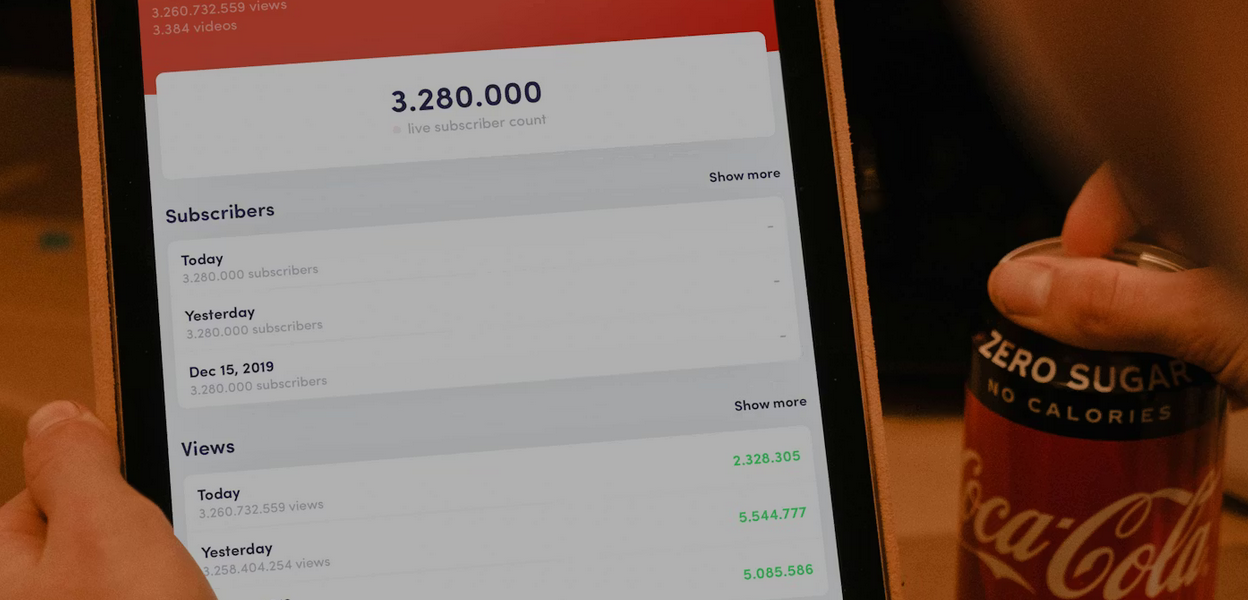
Many beginners overlook the powerful insights available through YouTube Analytics. Demographics, watch time, traffic sources, and retention data reveal who is engaging with content and how. Ignoring these metrics often leads creators to continue producing content that underperforms. Tracking analytics enables informed decisions, such as optimizing upload times, adjusting video length, and selecting topics that align with audience preferences. Leveraging these insights is essential for tech creators aiming to refine targeting, increase viewer satisfaction, and strengthen channel performance over time.
Misinterpreting Engagement Signals
Tech YouTubers frequently misread engagement signals such as likes, comments, and shares. High view counts alone don’t always indicate an engaged audience; retention and interaction are more valuable for growth. Beginners may celebrate views without recognizing low watch time or weak comment activity, which can misguide content planning. Evaluating which videos generate meaningful interaction helps creators focus on content that genuinely resonates, rather than chasing fleeting popularity. Engagement metrics provide a clear picture of audience interest, guiding creators to produce videos that encourage discussion, subscriptions, and repeat viewership.
Overlooking Platform-Specific Behavior

Each platform has its own user behavior patterns, and many tech YouTubers fail to consider them. For instance, viewers on YouTube Shorts consume content differently than they do long-form tutorials. Ignoring these differences can reduce effectiveness when targeting audiences across multiple video formats. Understanding which platforms, formats, and viewing habits your audience prefers allows creators to optimize content, thumbnail design, and posting schedules. Catering content to audience habits ensures viewers discover videos in ways that naturally fit their consumption patterns, boosting overall reach and visibility.
Neglecting Community Feedback
Finally, beginners often underestimate the value of listening to their audience. Comments, polls, and messages are direct sources of insight into viewer interests and pain points. Dismissing …



 Facebook loves knowing what you like—it’s how it keeps you scrolling. But the ad settings can be sneaky. Head to your settings and find the section on ads. Disable “activity outside Facebook,” and turn off categories that describe you. That way, you’re not feeding the beast every time you browse an online store. You’ll still get ads, but they’ll be less creepy and more random, which honestly feels like a win.
Facebook loves knowing what you like—it’s how it keeps you scrolling. But the ad settings can be sneaky. Head to your settings and find the section on ads. Disable “activity outside Facebook,” and turn off categories that describe you. That way, you’re not feeding the beast every time you browse an online store. You’ll still get ads, but they’ll be less creepy and more random, which honestly feels like a win.




 It all starts with a great idea. On the other hand, the idea that seems revolutionary to you essentially needs to be executed to turn into a successful thing. Therefore, the first and most important step in mobile growth would be to find out the purpose of your program and examine it from the facts. Determine the target audience of your app, where they are located, why they will download and use your app, what your competitors are offering for similar services or products, and what features your app should have. This analysis will take at least a day or two.
It all starts with a great idea. On the other hand, the idea that seems revolutionary to you essentially needs to be executed to turn into a successful thing. Therefore, the first and most important step in mobile growth would be to find out the purpose of your program and examine it from the facts. Determine the target audience of your app, where they are located, why they will download and use your app, what your competitors are offering for similar services or products, and what features your app should have. This analysis will take at least a day or two. While your app should have unique aspects, it shouldn’t be so special that no one else can handle it. You can skip the traditional learning curve associated with a new app if your screen users are comfortable with it. Your mobile app should include an easy and intuitive navigation or search function, especially if you have a large amount of content. Sharing on social media isn’t just for quick photos of cats and kids. Social networking programs have carved out a niche when it comes to communicating and collaborating with different people you know online, especially between employees who are geographically separated and between employees and their customers.…
While your app should have unique aspects, it shouldn’t be so special that no one else can handle it. You can skip the traditional learning curve associated with a new app if your screen users are comfortable with it. Your mobile app should include an easy and intuitive navigation or search function, especially if you have a large amount of content. Sharing on social media isn’t just for quick photos of cats and kids. Social networking programs have carved out a niche when it comes to communicating and collaborating with different people you know online, especially between employees who are geographically separated and between employees and their customers.…






 If you do not want to spend a considerable amount of money, we recommend looking for used audio equipment. If you search the Internet, you will find many stores on the Internet that have used the audio equipment. Most of them are in very good shape and can be used without any problems. Start looking for the best brands because they usually offer the best products. There are many stores on the Internet that allow you to compare goods, i.e., to compare prices, features, and other aspects that are important to you. But if you want to learn how to save money for audio equipment, visit
If you do not want to spend a considerable amount of money, we recommend looking for used audio equipment. If you search the Internet, you will find many stores on the Internet that have used the audio equipment. Most of them are in very good shape and can be used without any problems. Start looking for the best brands because they usually offer the best products. There are many stores on the Internet that allow you to compare goods, i.e., to compare prices, features, and other aspects that are important to you. But if you want to learn how to save money for audio equipment, visit  Another thing to consider before buying a sound system is whether you prefer to buy a wired or wireless system. Wireless systems are less expensive and much more suitable. They are easier to install, easier to use, and much better than wired systems.
Another thing to consider before buying a sound system is whether you prefer to buy a wired or wireless system. Wireless systems are less expensive and much more suitable. They are easier to install, easier to use, and much better than wired systems.




 Consumers prefer programs that are simple to use. They make room for simplicity directly. There are many programs on the internet for a user. Rather than analyzing your program, users will try to find an easier to use program. So, top program devs prefer to design their apps in such a manner that a 10-year old child will have the ability to browse through the program. It’s possible to choose some opportunity to research some successful programs. You may discover that most of them are extremely simple to comprehend and utilize, offering an excellent user experience.
Consumers prefer programs that are simple to use. They make room for simplicity directly. There are many programs on the internet for a user. Rather than analyzing your program, users will try to find an easier to use program. So, top program devs prefer to design their apps in such a manner that a 10-year old child will have the ability to browse through the program. It’s possible to choose some opportunity to research some successful programs. You may discover that most of them are extremely simple to comprehend and utilize, offering an excellent user experience. The amount of its consumers judges any app’s achievement. So program developers make sure their programs support both iOS and Android platforms. Then you have halved the odds of success if your program works on both. If your program works on the sole iOS, it means you’ve cut off most Android users and vice-versa. To make your application successful, it must be compatible with both Android and iOS.
The amount of its consumers judges any app’s achievement. So program developers make sure their programs support both iOS and Android platforms. Then you have halved the odds of success if your program works on both. If your program works on the sole iOS, it means you’ve cut off most Android users and vice-versa. To make your application successful, it must be compatible with both Android and iOS.
 There is a principle of program storage for iOS application developers, along with the rule that they must follow to design radio applications that achieve the rate. Because workers’ customers are more significant than many others, the program memory is overflowing with apps. The material discusses the best methods for this, such as the level of security. During discovery, along with tracking, developers create applications that do not contain threats.
There is a principle of program storage for iOS application developers, along with the rule that they must follow to design radio applications that achieve the rate. Because workers’ customers are more significant than many others, the program memory is overflowing with apps. The material discusses the best methods for this, such as the level of security. During discovery, along with tracking, developers create applications that do not contain threats. Developers need to update their applications. As time goes by, new threats …
Developers need to update their applications. As time goes by, new threats …
